Archives
IASbaba’s Daily Current Affairs – 9th March, 2016
DEFENCE/SECURITY
TOPIC:
General studies 3:
- Science and Technology - developments and their applications and effects in everyday life Achievements of Indians in science & technology; indigenization of technology and developing new technology.
- Challenges to internal security through communication networks, role of media and social networking sites in internal security challenges, basics of cyber security; money-laundering and its prevention.
General studies 2:
- Government policies and interventions for development in various sectors and issues arising out of their design and implementation.
Upgrading India’s cyber security architecture
- India’s National Cyber Security Policy aims to build a secure and resilient cyberspace for citizens, business and government.
- However the cyber security architecture in India lacks potential to regulate various cyber-crimes that happen.
Comparing digital space of India and the world:
Two things set aside India’s digital spaces from that of major powers such as the United States and China:
Design and Density
Design:
- India is a net information exporter.
- Its information highways point west, carrying with them the data of millions of Indians.
- This is not a design flaw, but simply reflects the popularity of social media platforms and the lack of any serious effort by the Indian government to restrict the flow of data.
Density:
- Equally important is the density of India’s cyberspace.
- Nearly 500 million Indians use the Internet today, but they do not access the Internet from the same devices.
- Apple’s market share in the U.S., for instance, is 44 per cent, but iPhones account for less than 1 per cent in India.
- The massive gap between the security offered by the cheapest phone in the Indian market and a high-end smart phone makes it impossible for regulators to set legal and technical standards for data protection.
Digital intrusions:
India’s infrastructure is susceptible to four kinds of digital intrusions:
- Espionage: Involves intruding into systems to steal information of strategic or commercial value.
- Cybercrime: Referring to electronic fraud or other acts of serious criminal consequence.
- Attacks: Intended at disrupting services or systems for a temporary period.
- War: Caused by a large-scale and systematic digital assault on India’s critical installations.
India lacks a national security architecture:
- Recognising the strategic dimensions of cyberspace, the Prime Minister’s Office (PMO) created the position of the National Cyber Security Coordinator in 2014, however it failed to deliver the various dimensions of cyber security.
- There is, however, no national security architecture today that can assess the nature of cyber threats and respond to them effectively.
- India’s civilian institutions have their own fire-fighting agencies, and the armed forces have their own insulated platforms to counter cyber-attacks.
- Overall India needs an agency to supervise the cyber security aspects.
What could such an agency look like?
- The first requirement is to house it with permanent and semi-permanent staff that is technically proficient in cyber operations, both defensive and offensive.
- India faces a shortage of officers trained in creating and breaking encrypted platforms as well as using digital networks for intelligence gathering.
- Were such a National Cyber Security Agency (NCSA) to be created, it should have a functional “nucleus” or secretariat.
- The second requirement is to coordinate the agency’s policy functions and operations.
- The current cyber security policy, articulated in 2013 by the Ministry of Communications and Information Technology, is basically a statement of first principles.
- The NCSA should be guided by a document outlining India’s cyber strategy, much like its nuclear doctrine.
- India should not hesitate to build its offensive cyber capabilities.
- This would involve the development of software designed to intrude, intercept and exploit digital networks.
- The deployment of cyber weapons is not a low-cost affair, as the digital trail allows adversaries to track and possibly predict the development of future technologies.
- Nevertheless, a cyber-arsenal serves the key function of strategic deterrence.
- India’s cyber command should be the primary agency responsible for the creation and deployment of such weapons.
Way ahead:
- A fully operational cyber command will take years to complete.
- It is the need of the hour, given that India’s digital capabilities lag significantly behind regional and global players.
- Whatever final form India’s cyber command takes, the government should do well to pursue the ultimate objective of a robust cyber security platform to fight digital intrusions.
Connecting the dots:
- Critically examine the need of a robust cyber security architecture for India to tackle the growing digital intrusions.
- Critically evaluate the provisions of National Cyber Security Policy 2013.
NATIONAL
TOPIC: General studies 2
- Government policies and interventions for development in various sectors and issues arising out of their design and implementation;
- Important aspects of governance, transparency and accountability, e-governance-applications, models, successes, limitations and potential
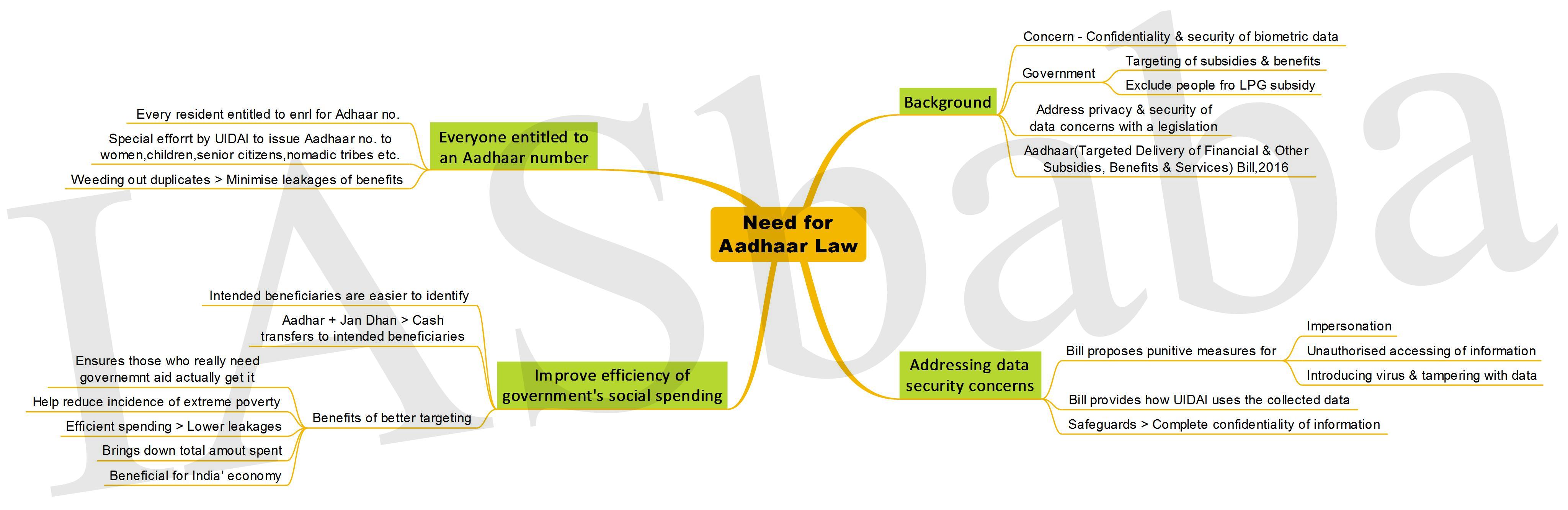
The Aadhaar Revolution
Aadhaar Project: An ambitious project that seeks to provide unique identification numbers to each individual in a country of over a billion people, collecting demographic and biometric information in the process
Aadhaar (Targeted Delivery of Financial and Other Subsidies, Benefits and Services) Bill, 2016: To provide for “efficient, transparent, and targeted delivery of subsidies, benefits and services”
Legislative Vacuum?
- Any advanced technology needs to be designed in a simple way to enable it to be used conveniently on an open platform, satisfying multiple stakeholders and ensuring privacy in the flow.
- The infrastructure, if properly developed can help government go paperless, presence-less and cashless; catapulting India to the front of the league of nations whose governments use technology to create an effective, efficient and modern welfare state that treats its people with dignity.
- But the question over the much-required legal validity for Aadhaar has garnered attention once again, with the Aadhaar Bill resting amidst many legal and political challenges and a change in government; being issued already for over 98 crore in numbers.
The regulatory legitimacy thus, is much sought after, to let it operate at its full potential.
Aadhaar Bill—
- Enrolment is voluntary; shall only be used as proof of identity and not as proof of citizenship
- Will enable the government to prevent fraud, corruption and waste by requiring the Aadhaar number for delivery of any benefit, subsidy or service from the Consolidated Fund of India, such as LPG subsidy, MGNREGA wages, various insurance schemes, provident fund schemes, government scholarships, and much more
- Does not prohibit the usage of Aadhaar for any other purpose by any public or private entity
- Provision of privacy protection –
- Use limitation— it can only be used for the purpose for which the user gives consent
- Collection limitation— no information other than demographic (name, address, date of birth, sex and, optionally, email id/ mobile number) and biometric (photo, fingerprint and iris scan) will be collected. No other personal information of an individual will be in the Aadhaar database
- Access and Rectification— the user can access his own information and has an obligation to rectify it if it needs updating
- No demographic information or identity information received from the Unique Identification Authority of India can be displayed publicly
- Only exception to certain confidentiality (but not security) obligations is national security: Provided an order to disclose information is issued either (limited time period)-
- By a court or
- By a joint secretary or
- Higher officer, and
- Vetted by a high-powered committee headed by the cabinet secretary
- No core biometric information can be shared is a principle without exception — people saying that core biometric information will be shared are wrong because Clause 29(1) is not overridden by Clause 33(2)
- Bill includes stringent penalties, including imprisonment for breach of privacy and other violations
Section 29(4)- No Aadhaar number or biometric information will be made public “except for the purposes as may be specified by regulations”
Section (33)- The inbuilt confidentiality clauses will not stand when it concerns national security
Potential:
- To be used as a powerful instrument against retail corruption
- To deepen financial inclusion
- To eliminate the usage of more than 2,000 crore pages of paper (a low guesstimate)
- Enable more than 300 million daily seekers of government services to save at least two hours every day
- Eliminate fraud in government subsidies of at least Rs. 50,000 crore every year
- Enable linking individuals to an organisation that has a unique enterprise number, shifting enforcement to big data
- Unclog our highways and eliminate waiting rooms in hospitals as well as eliminate fraud in degrees and substantially improve labour market matching
Way Ahead- Danger of “Digital Colonisation”:
- The concern over the increased access to the information over the internet is a matter to be seriously thought over as the ball going in the field of a few internet ‘gatekeepers’ tracking all our digital activities is extremely high.
- Therefore, need for the Aadhaar platform, to promise an open, secure and privacy-protected digital ID to a billion Indian residents to access the internet, will be a critical bulwark to ensure our digital independence.
Connecting the Dots:
- What do you mean by Digital Colonization? What are the steps that India can take to overcome the danger of digital colonisation?
MUST READ
Cooling the earth down
Constitution Bench to decide if MPs, MLAs can be disqualified upon framing of charges
Government cuts its losses on EPF
Related Articles:
Employees’ Provident Fund (EPF) Tax- Is it a Healthy proposal?
Cashing in on Libya’s power vacuum
Related Articles:
More Mollycoddling- Latest sale of F-16s by the US to Pakistan carries a message for India.
Raja-Mandala: Trading places- On the South China Sea, Delhi speaks less in public while Washington can’t stop talking.
Related Articles:
Protecting privacy in democracies
MIND MAPS
1. Need for Aadhaar Law