Archives
(PRELIMS Focus)
Category: Polity and Governance
Context:
- Recently, the Supreme Court struck down provisions of the Tribunal Reforms Act of 2021, a law designed to alter the tribunal system.

About Tribunal Reforms Act, 2021:
- Objective: The Act was enacted to streamline the functioning of tribunals by dissolving certain appellate tribunals and transferring their functions to existing judicial bodies like the High Courts.
- Associated SC Judgement: It was introduced in response to the Supreme Court’s ruling in the case of Madras Bar Association vs. Union of India (2021), which struck down certain provisions of the Tribunal Reforms (Rationalisation and Conditions of Service) Ordinance, 2021.
- Selection Committee for Central Tribunals:
- Chairperson: Chief Justice of India (CJI) or a Supreme Court judge nominated by the CJI (casting vote).
- Two Secretaries nominated by the Central Government.
- Sitting/outgoing Chairperson of the tribunal, or a retired Supreme Court judge, or a retired Chief Justice of a High Court.
- Non-voting member: Secretary of the relevant Union Ministry.
- Selection Committee for State Administrative Tribunals:
- Chairperson: Chief Justice of the respective High Court (casting vote).
- Chief Secretary of the State Government.
- Chairman of the State Public Service Commission.
- Sitting/outgoing Chairperson of the Tribunal or a retired High Court Judge.
- Tenure of members: The tenure for Chairperson and Members is 4 years, with a minimum age of 50 years. The maximum age limit is 67 years for tribunal members and 70 years for chairpersons, or completion of the 4-year tenure, whichever is earlier.
- Members eligible for reappointment: Tribunal Chairpersons and Members are eligible for reappointment, with preference given to their past service.
- Removal of Tribunal Members: Central government on the recommendation of the Search-cum-Selection Committee can remove Chairperson or a Member.
About SC Observations and Rulings:
- The Bench of Chief Justice B.R. Gavai and Justice K. Vinod Chandran held that the 2021 Act was an attempt to “repackage” the very provisions earlier invalidated.
- The Court noted that Parliament cannot circumvent judicial directions by re-enacting an unconstitutional provision in slightly modified form.
- The Court found the 2021 Act to be a “legislative override” that consciously defied earlier judgments relating to tribunal autonomy.
- The Supreme Court invalidated provisions that:
- Allowed the Centre to control tenure and age limits of tribunal members,
- Included government secretaries on the selection committee,
- Limited tenure to four years, undermining institutional stability,
- Granted excessive rule-making powers to the executive over tribunals.
Source:
Category: Science and Technology
Context:
- ISRO has successfully demonstrated the bootstrap mode start test on the CE20 cryogenic engine which powers the upper stage of the Launch Vehicle Mark-3 rocket.

About CE20 Cryogenic Engine:
- Development: It is a cryogenic rocket engine developed by the Liquid Propulsion Systems Centre, a subsidiary of the Indian Space Research Organisation (ISRO).
- Objective: It is used to power the upper stage of the LVM3 launch vehicle and has been qualified to operate at a thrust level of 19 tonnes. This engine has also successfully powered the upper stage of six LVM3 missions so far.
- Uniqueness: It is the first Indian cryogenic engine to have a gas-generator cycle. The CE-20 uses a combination of LOX and LH2 propellants in a gas generator cycle.
- Significance: It marks a significant step in ISRO’s indigenous engine development, showcasing its ability to overcome complex rocket propulsion challenges.
- Mechanism: During nominal operation, the engine ignition is initiated under tank head conditions, followed by the start of turbo pumps using a stored gas start-up system.
- Important for LVM3 flights: The test on the CE20 cryogenic engine, which was successfully conducted under vacuum conditions in the High-Altitude Test (HAT) facility at ISRO Propulsion Complex, Mahendragiri is an important development towards enhancing the restart capability and mission flexibility of future LVM3 flights.
- Qualified for important missions like Gaganyaan: The CE20 cryogenic engine, powering the LVM3 upper stage, is already qualified for operation at thrust levels ranging from 19 to 22 tonnes in flight with a single start, and also for the Gaganyaan missions.
- Essential for flexible multi-orbit missions: For future missions, multiple in-flight restarts of the CE20 engine will be needed for flexible multi-orbit missions.
- Exploring possibility of bootstrap mode start: With the current set-up, each restart demands an additional start-up gas bottle and associated systems. Hence, achieving bootstrap mode start, where the engine builds up to steady operation without external start-up assistance is essential.
Source:
Category: International Organisations
Context:
- The Gulf Cooperation Council has approved a landmark one-stop travel system designed to streamline movement across member states.
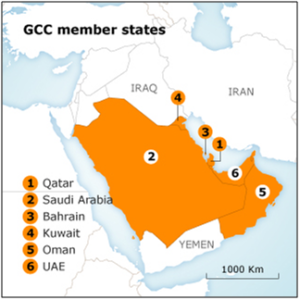
About Gulf Cooperation Council (GCC):
- Establishment: It is a regional political and economic alliance established in 1981.
- Members: The member countries include Bahrain, Kuwait, Oman, Qatar, Saudi Arabia, and the United Arab Emirates (UAE).
- Objective: It aims to foster economic, security, cultural, and social cooperation among its members. This cooperation is based on common Islamic values, tribal links, and mutual security and development goals.
- History: It was formed in response to escalating regional tensions, particularly the Iranian Revolution (1979) and the Iran-Iraq War (1980–1988).
- Headquarters: Its headquarters is located in Riyadh, Saudi Arabia.
- Significance: GCC countries are located strategically along the Persian Gulf, linking Europe, Asia, and Africa through maritime routes. Further, the bloc controls around 30% of global oil reserves and is a major exporter of natural gas.
- Organizational Structure: Supreme council is the highest authority of the GCC, composed of the heads of the member states. Ministerial council is composed of foreign ministers or their representatives from member states. It proposes policies and implements decisions of the Supreme Council.
- About One-stop Travel System:
- It is part of the GCC’s ambitious push to eliminate redundant travel procedures and foster stronger cooperation between member states.
- It will allow Gulf citizens to complete all travel procedures including immigration, customs and security checks at a single checkpoint.
Source:
Category: Miscellaneous
Context:
- Farmers in Uttar Pradesh are seeing their dreams take flight with the revival as BHU researchers revive timeless rice variety ‘Adam Chini’ with innovation.

About Adam Chini Rice:
- Nature: It is an aromatic black rice variety known for its pleasant aroma and superior cooking qualities. It received Geographical Indication (GI) in 2023.
- Growing areas: It is mainly grown in the Eastern Uttar Pradesh region including Chandauli, Varanasi and Vindhya region.
- GI tagged: It received Geographical Indication (GI) status on 22 February 2023 (valid till November 2030). The GI tag proposed by Ishani Agro Producer Company Ltd. and Human Welfare Association of Uttar Pradesh.
- Uniqueness: It is known for its sugar-crystal-like grains, drought tolerance, and disease resistance qualities. It has long maturity period (155 days) and low yields (20-23 quintals per hectare).
- Structure: It reaches height up to 165 cm and its grains are short-bold, scented with intermediate alkali digestion value.
- Presence of amylose: It has intermediate amylose content which helps rice to remain fluffy and remains soft on cooling. It is renowned for its excellence in flavour.
- Improved features by BHU:
- Reduced height (105 cm for mutant-14),
- Early maturity (120 days for mutant-19),
- Higher yields (30-35 quintals per hectare for mutants 14, 15, 19, and 20).
- Now it is more suitable for mass production while retaining its coveted fragrance.
Source:
Category: Defence and Security
Context:
- The eighth edition of the India-UK Joint Military Exercise ‘Ajeya Warrior-25’ commenced at the Foreign Training Node, Mahajan Field Firing Ranges, Rajasthan.

About Exercise Ajeya Warrior:
- Nature: It is a bilateral military exercise conducted between India-UK.
- Commencement: It is held biennially since 2011, AJEYA WARRIOR has evolved into a flagship engagement between the Indian Army and the British Army.
- Objective: The objective of the exercise is to facilitate the exchange of best combat skills and experiences between the two armies and to enhance their ability to operate together in complex situations.
- Uniqueness: It is conducted under a United Nations mandate, specifically aligned with Chapter VII of the UN Charter, which deals with peacekeeping duties related to threats to peace, breaches of peace, and counter-terrorism scenarios.
- Significance: The exercise further reinforces shared values of professionalism, cooperation and commitment to regional stability and global peace.
- About Exercise Ajeya Warrior 2025:
- The Indian Army is being represented by troops of the Sikh Regiment.
- It includes joint mission planning at Brigade level, integrated tactical drills, simulation-based scenarios and company-level field training exercises replicating real-life counter-terror contingencies.
- The exercise also aims to share best practices, enhance tactical proficiency and develop coordinated responses for managing complex operations in challenging environments.
Source:
(MAINS Focus)
(GS Paper III – Internal Security: Left-Wing Extremism, Security Forces, Governance & Development)
Context (Introduction)
The killing of top Maoist commander Madvi Hidma in Andhra Pradesh marks a turning point in India’s two-decade struggle against Left-Wing Extremism (LWE). Improved policing, leadership targeting, and development efforts have sharply shrunk Maoist influence across the Red Corridor.
Main Arguments
- Shift from Maoist dominance to State control: In the early 2000s, PWG cadres held vast tribal-forest belts from Andhra Pradesh to Nepal — termed the “Compact Revolutionary Zone.” Maoists controlled interiors due to weak governance and favourable terrain.
- Political ambiguity enabled regrouping: States, especially Andhra Pradesh in 2004, alternated between police withdrawal and peace talks. Ceasefires allowed Maoists to consolidate, culminating in the 2004 PWG–MCC merger forming CPI (Maoist).
- Severe constraints on early security operations: Forces lacked anti-mine vehicles, fortified police stations, and helicopter support. Stints in Maoist zones were viewed as punishment postings. Intelligence suffered due to lack of local-language capacity.
- Escalation of Maoist violence (2006–2013): Attacks intensified: the Tadmetla ambush killed 76 CRPF personnel (2010) and the 2013 Jhiram Ghati attack wiped out Chhattisgarh’s Congress leadership. Affected districts reached 126 in 2013.
- Strategic overhaul since 2014: The Centre prioritised modernisation of forces, strengthened inter-State coordination, choked financing networks, targeted top leadership, and expanded welfare schemes. Affected districts reduced to 38 (2024) and now to just 11.
Criticisms / Drawbacks/Limitations
- Treating LWE merely as a law-and-order problem: Early policies underestimated its ideological and armed revolutionary character, resulting in slow, inconsistent State responses.
- Ceasefire missteps and political signalling: Talks without verification mechanisms enabled Maoists to regroup, recruit, and rearm — reversing earlier operational gains.
- Weak grassroots policing infrastructure: Insufficient police stations, poor road networks, and scarce local recruitment limited State presence in remote tribal belts.
- Persistent governance vacuum in interiors: Slow progress in roads, schools, telecom, and welfare schemes allowed Maoists to position themselves as parallel authorities.
- Maoist adaptability to terrain and borders: Dense forests, tri-junction borders (AP–Chhattisgarh–Odisha), and tribal alienation provided operational and social cover for cadres.
Reforms and Way Forward
- Strengthen Local Policing & Intelligence
- Expand fortified police stations in interior tribal zones.
- Recruit local youth fluent in dialects for intelligence.
- Replicate Greyhounds and C-60–style specialised units nationally.
- Technology-driven Operations
- Scale use of drones, satellite mapping, helicopter mobility, and anti-landmine vehicles.
- Build integrated command systems across affected tri-junctions.
- Leadership Targeting & Financial Disruption
- Sustain operations removing top leaders and active dalams.
- Target extortion, illegal mining, and forest-produce revenue streams.
- Address Governance Deficits
- Accelerate Special Central Assistance for roads, telecom, health and education.
- Ensure fast compensation and grievance redressal in conflict-hit areas.
- Expand power supply, banking access, and digital services.
- Community-Centric Development & Rehabilitation
- Promote tribal welfare, forest rights implementation, and participatory planning.
- Strengthen surrender, rehabilitation, and livelihood programmes.
- Counter Maoist narratives through local influencers and SHG networks.
Conclusion
Two decades after being termed India’s “single biggest internal security challenge,” Left-Wing Extremism is in visible retreat. The convergence of improved policing, targeted operations, and expanding development has fractured Maoist organisational capacity. Yet, sustaining gains requires deep governance penetration, empowered tribal communities, and continued vigilance to prevent resurgence.
Mains Question
- Left-Wing Extremism has seen a marked decline in recent years. Analyse the factors behind this trend and suggest measures to consolidate the gains achieved. (250 words, 15 marks)
Source: The Indian Express
(GS Paper III – Internal Security: Terrorism, Cybersecurity, Encrypted Communication, Counter-Radicalisation)
Context (Introduction)
The Red Fort car blast in Delhi on November 10, which killed 15 people, has exposed a new frontier in terrorism where extremist cells combine encrypted digital tools, private servers, and spy-style communication to evade surveillance and coordinate attacks.
Main Arguments
- Use of high-privacy encrypted apps: Investigators found that the accused used Threema, an E2EE messaging app that requires no phone number and leaves minimal metadata. The module may have operated from a private Threema server, enabling isolated, untraceable communication.
- Adoption of digital “dead-drop” emails: The cell reportedly used shared email accounts in which drafts (not sent messages) were updated and deleted — a classic espionage method leaving no communication trail, bypassing phone or email logging systems.
- Sophisticated operational planning: The group conducted multiple reconnaissance missions using routine vehicles, stockpiled ammonium nitrate, and maintained disciplined communication gaps after arrests — reflecting a professional understanding of counter-surveillance.
- External ideological or operational linkages: Preliminary leads suggest possible ties with or inspiration from Jaish-e-Mohammed (JeM). The communication architecture — encrypted apps, dead-drop emails, minimal digital footprint — indicates high-level training and organisational backing.
- Alignment with global academic research: Scholarship repeatedly warns that extremist actors increasingly exploit E2EE platforms, VPNs, and decentralised networks, combining physical tradecraft with digital anonymity in ways that weaken traditional counter-terrorism tools.
Criticisms / Drawbacks/Limitations
- Limitations of traditional surveillance: Phone tapping, metadata analysis, and email intercepts become ineffective when extremists use private servers, VPNs, and apps with zero metadata retention.
- Regulatory gaps on self-hosted platforms: Banning Threema (under IT Act Sec 69A) has limited impact because terror modules use VPNs and offshore hosting. Law enforcement lacks a framework to monitor private encrypted servers.
- Inadequate cyber-forensics capability: Many agencies still rely on device seizure rather than advanced memory forensics, server-side analysis, or encrypted-network mapping.
- Failure to detect radicalisation in professional spaces: The involvement of medical professionals from a university shows that radicalisation can occur among highly educated individuals, where existing monitoring or awareness systems are weak.
- Risks of transnational networks: If external handlers are confirmed, India faces challenges in securing cross-border cooperation, especially where encrypted infrastructure is located abroad.
Reforms and Way Forward
- Build specialised digital-forensics and cyber-intelligence units
- Expand teams skilled in decrypting memory dumps, analysing E2EE misuse, and tracking private servers.
- Train personnel in dark-web monitoring, digital dead-drop detection, and server-level forensics.
- Strengthen NIA and State ATS cyber labs with modern tools.
- Regulate self-hosted encrypted infrastructure
- Create frameworks requiring private communication servers to maintain minimal lawful-access compliance.
- Establish judicially supervised protocols for cooperation with providers of encrypted apps.
- Track VPN exit nodes and anonymisation networks linked to terror activity.
- Modernise legal frameworks for digital terrorism
- Amend counter-terrorism laws to recognise encrypted dead-drops, decentralised communication, and private servers.
- Mandate detection of high-risk shared accounts or draft-only mailboxes in investigations.
- Strengthen admissibility standards for cyber-forensic evidence.
- Strengthen institutional and community vigilance
- Equip universities, hospitals, and professional bodies with counter-radicalisation resources.
- Launch targeted awareness programmes for high-skill sectors vulnerable to ideological recruitment.
- Build early-warning mechanisms through counselling cells, faculty training, and student support networks.
- Deepen international cooperation
- Engage foreign governments, cybersecurity entities, and encrypted-app host countries through tech diplomacy.
- Enhance intelligence sharing on E2EE misuse, server hosting, funding routes, and cross-border handlers.
- Partner with global cyber-forensics centres for training and joint operations.
Conclusion
The Red Fort blast demonstrates that modern terrorism is increasingly digital, decentralised, and encrypted. As extremist cells adopt sophisticated tradecraft across physical and virtual domains, India must expand cyber-forensics, regulate private encrypted infrastructure, strengthen institutional vigilance, and collaborate globally. Counter-terrorism now requires not only boots on the ground, but also capability in code, servers, and encrypted networks.
Mains Question
- The Red Fort blast highlights how encrypted communication and digital tradecraft are reshaping terrorism. Examine how such technologies complicate counter-terrorism efforts and suggest reforms to strengthen India’s digital security architecture.(250 words, 15 marks)
Source: The Hindu
