Archives
(PRELIMS Focus)
Category: Defence and Security
Context:
- Recently, the 14th edition of the annual India-Maldives bilateral Exercise Ekuverin started in Thiruvananthapuram, Kerala.

About Exercise Ekuverin:
- Nomenclature: The Exercise ‘Ekuverin’ meaning ‘Friends’ in Dhivehi language started in the year 2009.
- Countries involved: Ekuverin is one of the three major joint exercises between India and the Maldives.
- Launch year: It is a bilateral military annual exercise conducted alternatively in India and Maldives since 2009.
- Objective: The Exercise aims to enhance interoperability while carrying out counterinsurgency and Counter Terrorism operations in semi-urban, jungle and coastal terrain.
- Significance: Exercise Ekuverin continues to be a shining example of India’s Neighbourhood First Policy and its commitment to building enduring defence partnerships with friendly nations.
- Focus areas: It focuses on integration of niche technology to enhance interoperability, the countries will share best practices, reflecting the shared commitment of India and the Maldives towards peace and security in the region.
- Important for Indian Ocean region: The exercise reflects the growing defence cooperation and mutual commitment of India and the Maldives towards regional peace and stability in the Indian Ocean Region.
- Other Exercises between India and Maldives: The two bilateral exercises are “Ekuverin” and “Ekatha” and trilateral- “Dosti”, which includes Sri Lanka.
About Exercise Ekuverin 2025:
- The Indian Army contingent of 45 personnel, represented by a battalion of the Garhwal Rifles, is participating alongside an equal-strength Maldivian contingent represented by the MNDF.
- The two-week-long exercise aims to enhance interoperability and operational synergy in Counter-Insurgency and Counter-Terrorism operations across jungle, semi-urban and coastal terrain.
- It will witness participation of troops from both sides sharing best practices, tactical drills and joint operational planning to strengthen their capability to respond to common security challenges in the region.
Source:
Category: History and Culture
Context:
- Nagaland’s Hornbill Festival, began recently amid renewed pushback by the state government against the Centre’s re-imposition of the Protected Area Regime.

About Hornbill Festival:
- Nomenclature: It was named after the Hornbill bird is named after the hornbill bird, a symbol of fidelity, beauty, and grace in Naga folklore.
- Location: It is celebrated at Naga Heritage Village, Kisama which is about 12 km from Kohima in Nagaland.
- Launch year: It was first organized in the year 2000 and it showcases the heritage of its 17 Naga tribes.
- Objective: It aims to promote inter-tribal interaction and preserve Nagaland’s heritage, blending the traditional with the contemporary in a harmonious display of unity.
- Significance: It is also called the festival of festivals and is held every year.
- Organising authority: It is organized by the State Tourism and Art & Culture Departments of the Government of Nagaland.
- Evolution: It has evolved into a celebration showcasing the diverse and vibrant cultural and traditional heritage of the tribes of Nagaland. It serves as a platform for the Naga tribes to display their rich traditions through performances, dances, and exhibitions.
- Distinctive attire: Warriors, dressed in full ceremonial attire, perform traditional dances and war cries that narrate stories of victories, harvests, love, and tribal legends. Their distinctive attire features hornbill feathers, boar tusks, and colourful woven sashes, creating a striking display of Naga heritage and pride.
About Hornbill Festival 2025:
- Theme of 2025 festival: Cultural Connect
- This year Nagaland has officially named Switzerland and Ireland as country partners for the Hornbill Festival 2025.
Source:
Category: International Organisations
Context:
- India has been re-elected to the Council of the International Maritime Organization (IMO) in Category B, which includes 10 countries.

About International Maritime Organization (IMO):
- Nature: IMO is the global standard-setting authority for the safety, security, and environmental performance of international shipping.
- Objective: Its main role is to create a regulatory framework for the shipping industry that is fair and effective, universally adopted, and universally implemented.
- Headquarters: Its headquarters is located in London.
- Membership: It has 176 Member States and three Associate Members. Once a member state adopts a regulation, it becomes part of that country’s domestic law.
- Funding mechanism: Funding is sourced through mandatory contributions by member states and also from voluntary donations and commercial revenue.
- Association with UN: It is the United Nations’ specialised agency responsible for the safety and security of shipping and the prevention of marine pollution by ships.
- Lacks enforceability of laws: The IMO formulates regulations on shipping safety, maritime security, and environmental protection but does not enforce them.
- Promotes SDG 14: It contributes directly to UN Sustainable Development Goal (SDG) 14, which focuses on the conservation and sustainable use of oceans and marine resources.
- Deals with legal issues: The organisation also deals with legal matters such as liability, compensation, and facilitation of maritime traffic.
- Organisational Structure: The Assembly is the supreme governing body, comprising all member states. It meets every two years to approve the work programme, budget, and elect members to the Council. The Council acts as the Executive Organ, overseeing IMO’s work in between Assembly sessions.
- Major Committees: The IMO has five major committees, which are responsible for policy development and regulation formulation, including the Marine Environment Protection Committee (MEPC).
Source:
Category: Science and Technology
Context:
- Cases of norovirus, commonly known as the “winter vomiting disease,” have been rising in the United States in recent weeks.
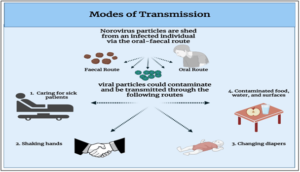
About Norovirus Disease:
- Nature: It is a common and highly contagious virus that causes inflammation in the stomach and intestines, a condition known as gastroenteritis.
- Other names: It is also sometimes referred to as the ‘stomach flu’ or the ‘winter vomiting bug’ as norovirus outbreaks usually happen seasonally in colder months.
- Vulnerable people: People of all ages can get infected and sick with norovirus, which spreads very easily and quickly.
- Frequency: One can get norovirus illness many times in your life because there are many different types of noroviruses. These viruses are responsible for about 90% of viral gastroenteritis outbreaks and close to 50% of cases across the world.
- Transmission: One can get norovirus from an infected person, contaminated food or water, or by touching contaminated surfaces. Norovirus infection occurs most frequently in closed and crowded environments.
- Symptoms: These include vomiting, diarrhoea, stomach cramps, nausea, fever, and tiredness. In extreme cases, loss of fluids could lead to dehydration.
- Treatment: Most people recover completely without treatment. No vaccines are currently available to prevent norovirus. Treatment for the infection focuses on relieving the symptoms.
- Prevention: Hands should be washed frequently with soap and water for at least 20 seconds. Further, contaminated surfaces should be disinfected with a bleach-based solution, especially in outbreak situations.
Source:
Category: Government Initiatives
Context:
- The Department of Telecommunications has ordered phone makers to pre-install the Sanchar Saathi app on smartphones by March 2026.

About Sanchar Saathi:
- Development: Sanchar Saathi is a is a security and awareness platform developed by the Department of Telecommunications (DoT).
- Availability: It is available both as an app and a web portal.
- Objective: It primarily aims to help mobile users manage their digital identity, report suspicious activity, and safeguard their devices.
- Focus on awareness: The platform also provides educational material on telecom safety and cyber risks, making it a combined service-and-awareness system.
- Chakshu Feature: It lets users report suspicious calls, SMS, and WhatsApp messages, such as fake KYC alerts, impersonation scams, or phishing links. It helps authorities spot fraud patterns.
- Addresses spam calls and links: Users can report spam calls and messages that break TRAI rules. Complaints made within seven days can lead to action against the sender. It also allows reporting of phishing links, unsafe APKs, and fraudulent websites.
- Checks linked mobile connections: It shows how many mobile numbers are registered using one’s identity. It also helps identify SIM cards taken without one’s knowledge.
- Blocks lost or stolen phones: It allows users to block the IMEI of a lost or stolen device so it can’t be used. Phones can be unblocked if recovered.
- Verifies authenticity of a device: It allows users to check if a phone is genuine by validating its IMEI. It is useful when buying second-hand phones.
- Reports fraud international calls: Some scammers use illegal telecom setups to make international calls appear as regular +91 calls. Sanchar Saathi enables users to report such cases.
- Verifies trusted contacts: It provides a directory to confirm genuine customer-care numbers, emails, and websites of banks and other major institutions.
Source:
(MAINS Focus)
(UPSC GS Paper II – “International Relations: India and its Neighbourhood, Regional Groupings, Security Architectures”) & GS Paper III – “Maritime Security, Internal Security Challenges”)
Context (Introduction)
The 7th NSA-level Colombo Security Conclave (CSC) summit in 2025 reflects India’s efforts to build a cooperative security framework in the Indian Ocean, as regional geopolitics, China’s growing footprint, and non-traditional maritime threats reshape strategic priorities.
Main Arguments
- Regional Security Platform: CSC provides a dedicated Indian Ocean security forum, unique in a region lacking a unified architecture despite high maritime vulnerabilities.
- Evolution of the Group: Originally a trilateral (India–Sri Lanka–Maldives), CSC expanded to include Mauritius (2022), Bangladesh (2024), and Seychelles (2025), signalling widening trust and strategic convergence.
- Addressing Non-Traditional Threats: The platform prioritises maritime security, counter-terrorism, trafficking, organised crime, and cyber threats, central to the economic and livelihood needs of littoral states.
- Development–Security Link: For CSC members, maritime security is inseparable from blue economy prospects, fisheries protection, disaster resilience, and sea-borne trade.
- India’s Strategic Moment: The summit strengthens India’s leadership at a time when the Indo-Pacific security environment is shifting due to China’s expanding influence and geopolitical volatility.
Challenges / Criticisms
- China Divergence: India views China’s presence in the Indian Ocean as a strategic risk, but many CSC members depend on China economically and do not share New Delhi’s threat assessment.
- Institutional Weakness: CSC still functions primarily through NSA-level meetings, lacking a deeper, standing institutional mechanism for sustained cooperation.
- Domestic Uncertainties: Political instability in key states, especially Bangladesh, may affect continuity of engagement and weaken long-term group cohesion.
- Fragmented Regional Architecture: The Indian Ocean remains divided among multiple, overlapping but weak security groupings, diluting collective action.
- Uneven Capacity: Smaller island states lack resources for maritime domain awareness, search-and-rescue, and cyber defence, limiting CSC’s effectiveness.
Way Forward
- Institutionalisation: Create permanent secretariat, working groups, and annual joint exercises, similar to ASEAN-led mechanisms, ensuring policy continuity.
- Capacity Building: India can expand IT, maritime domain awareness (MDA), and coast guard training through IORA, SAGAR, and I4F initiatives.
- Balanced China Strategy: CSC should frame cooperation around non-traditional security, avoiding overt anti-China signalling to maintain consensus among smaller states.
- Economic-Security Integration: Promote blue economy partnerships, port security, anti-piracy collaboration, and disaster preparedness, reflecting member priorities.
- Incremental Expansion: Gradually include Malaysia (guest in 2025) and other Indian Ocean states, ensuring the group grows without overstretching.
Conclusion
The CSC has emerged as a promising mini-lateral model for Indian Ocean security governance, overcoming historical fragmentation. Its future strength will depend on institutional resilience, balanced strategic messaging, and sustained cooperation that aligns security priorities with the developmental needs of littoral states.
Mains Question
- “The Colombo Security Conclave is becoming a crucial pillar of India’s maritime diplomacy but faces structural and geopolitical challenges.” Discuss. (250 words, 15 marks)
Source: The Hindu
(UPSC GS Paper II – “Fundamental Rights; Government Policies; Right to Privacy”;
GS Paper III – “Cybersecurity; Internal Security; Technology & Threats”)
Context (Introduction)
To curb cybercrime—from digital arrests to spoofed IMEI frauds—the government has mandated SIM binding and compulsory pre-installation of the Sanchar Saathi app on all new smartphones. The move has raised concerns over privacy, proportionality, and potential surveillance misuse.
Main Arguments:
- Cybercrime Escalation: Scams involving government impersonation, digital arrests, and cross-border networks have intensified, exploiting gaps in SIM-based verification systems.
- Account Exploitation: User accounts remain active even after SIM removal, enabling criminals to operate anonymously on encrypted messaging platforms.
- IMEI Spoofing: Counterfeit devices and tampered IMEI numbers have made tracking cybercriminals extremely difficult for law enforcement.
- Security Patch Intent: SIM binding aims to disable messaging app access when the associated SIM is removed, reducing impersonation risk.
- Device Verification Goal: Sanchar Saathi is intended to authenticate devices and weed out cloned or illegal handsets, strengthening the digital identification ecosystem.
Challenges / Criticisms
- Privacy Intrusion: The directive mandates that the app be pre-installed, visible, and undeletable, requiring higher security privileges, risking intrusive access.
- Surveillance Concerns: Elevated permissions could create a Panopticon-like tool, enabling continuous monitoring or exploitation—especially worrying given past use of Pegasus.
- Legality & Proportionality Issues: Under K.S. Puttaswamy (2017), state actions must satisfy legality, necessity, and proportionality. Existing alternatives make the measure disproportionate.
- Security Vulnerability: A privileged government app could become a high-value target for hackers, exposing millions of users to systemic risks.
- Industry Pushback: Privacy-focused companies like Apple have resisted compliance, signalling global discomfort with mandatory surveillance-linked applications.
Way Forward
- Privacy-by-Design Tools: Strengthen USSD codes, SMS checks, and web-based verification instead of forcing device-level intrusive apps.
- Targeted IMEI Regulation: Improve CEIR (Central Equipment Identity Register) functioning, coupled with telecom audits and stricter KYC enforcement.
- Risk-Graded Measures: Apply intrusive tools only for high-risk cases after judicial authorisation, not for every smartphone buyer.
- Independent Oversight: Create a privacy and cybersecurity review board, ensuring safeguards before deploying government apps on private devices.
- Transparent Standards: Publish data handling policies, permissions, and audit logs, ensuring that no invisible surveillance architecture is embedded into devices.
Conclusion
Cybercrime demands strong action, but compulsory government apps with privileged access raise grave concerns for privacy and constitutionalism. A sustainable cybersecurity strategy must rely on least-intrusive tools, transparent safeguards, and adherence to the proportionality doctrine laid down in Puttaswamy.
Mains Question
- “The compulsory installation of the Sanchar Saathi app aims to curb cybercrime but raises serious concerns under the privacy framework.” Examine. (250 words, 15 marks)
Source: The Hindu
